Active directory Penetration Testing
Compromise Active Directory,
compromise every user - it's that simple.
Misconfigurations and weaknesses in implementation can leave Active Directory vulnerable to breaches that could potentially compromise all your networked resources. Diligent configuration management, regular auditing for compliance with best practices, and a proactive approach to patching known vulnerabilities help maintain a robust security posture the entire network.
Weak Authentication & Credential Management (password policies, credential exposure)
Privilege Escalation Risks (misconfigured roles, excessive permissions)
Lateral Movement & Kerberoasting Attacks (service account abuse)
Active Directory Misconfigurations (unprotected admin groups, ACL flaws)
Unsecured LDAP & SMB Services (man-in-the-middle attacks)
Kerberos & NTLM Weaknesses (relay attacks, downgrade attacks)
GPO Misconfigurations (privilege escalation via policy manipulation)
Lack of Logging & Monitoring (undetected brute force, AD enumeration)
Compromise Active Directory,
compromise every user - it's that simple.
Misconfigurations and weaknesses in implementation can leave Active Directory vulnerable to breaches that could potentially compromise all your networked resources. Diligent configuration management, regular auditing for compliance with best practices, and a proactive approach to patching known vulnerabilities help maintain a robust security posture the entire network.
Weak Authentication & Credential Management (password policies, credential exposure)
Privilege Escalation Risks (misconfigured roles, excessive permissions)
Lateral Movement & Kerberoasting Attacks (service account abuse)
Active Directory Misconfigurations (unprotected admin groups, ACL flaws)
Unsecured LDAP & SMB Services (man-in-the-middle attacks)
GPO Misconfigurations (privilege escalation via policy manipulation)
Kerberos & NTLM Weaknesses (relay attacks, downgrade attacks)
Lack of Logging & Monitoring (undetected brute force, AD enumeration)
Hardening Your Active Directory Systems Using Proven Security Frameworks
Our assessment evaluates whether an attacker can:
Obtain Unauthorised Access
Obtain unauthorised access via credential theft or password spraying.
Escalate Privileges
Escalate privileges using misconfigured service accounts or delegation flaws.
Lateral Movements
Move laterally across the network using NTLM/Kerberos relay attacks.
Exploit AD Misconfigurations
Exploit AD misconfigurations to gain persistent access.
Exfiltrate Data
Exfiltrate sensitive AD data through enumeration techniques.
Actionable Recommendations You Can Bring To Stakeholders
We deliver comprehensive, cryptographically signed penetration testing reports that are both verifiable and tamper-proof. Each report includes detailed vulnerability backgrounds, clear impact assessments, and actionable recommendations. And because security is a global concern, our reports are available in 113 languages—ensuring your cross-border teams are always in the know.
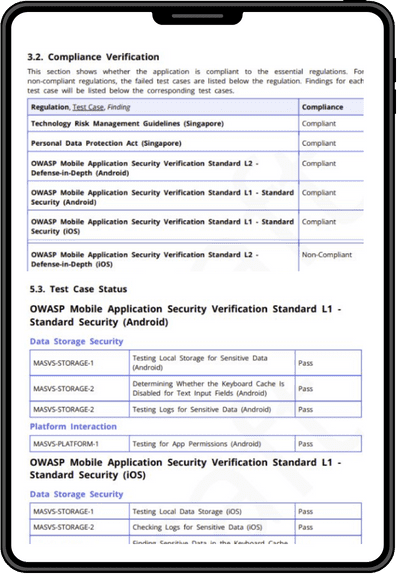
Compliance Verification Reporting
The report clearly shows the specific standards the app complies to.
Detailed down to the Test Cases

Detailed Background
We explain the vulnerability clear enough for technical and non technical stakeholders to understand.
Impact statements
Explaining the business impact of the vulnerability.
Recommendations
Actionable insights stakeholders can take to remediate gaps.
SPEAK TO AN EXPERT
Know Your Vulnerabilities.
Start Securing your Assets Today.
Experts in Penetration Testing
innovation and IP development
Red Team Providers in Southeast Asia
80,000+ hours of yearly pentesting
Specialists in AppSec
Quality Assurance with Velocity
Other CREST Approved Penetration Testing Services
Web Application
We secure your web applications by identifying injection flaws, authentication bypasses, and business logic vulnerabilities that could expose your systems, ensuring compliance to technical and regulatory standards.
Mobile Application
We secure your iOS and Android applications by identifying code vulnerabilities, insecure data storage, and authentication flaws, ensuring compliance to standards like the OWASP MASVS and more.
Wireless Network
We secure your Wi-Fi and wireless communication systems through targeted testing that identifies encryption flaws, authentication weaknesses, and connection protocol vulnerabilities.
API
We secure your APIs against data breaches and unauthorized access by identifying authentication flaws, injection vulnerabilities, and more in your API endpoints, ensuring compliance to standards like OWASP Top 10 and more.
Thick Client
We secure your desktop applications through thorough testing that identifies local storage vulnerabilities, communication protocol weaknesses, and authentication flaws that could compromise user data.
Active Directory
We secure your Active Directory infrastructure through specialized testing that identifies privilege escalation paths, credential vulnerabilities, and configuration weaknesses that could lead to domain compromise.
Other CREST Approved Penetration Testing Services
Mobile Application
We secure your iOS and Android applications by identifying code vulnerabilities, insecure data storage, and authentication flaws, ensuring compliance to standards like the OWASP MASVS and more.
Web Application
We secure your web applications by identifying injection flaws, authentication bypasses, and business logic vulnerabilities that could expose your systems, ensuring compliance to technical and regulatory standards.
Network
We secure your network infrastructure by identifying misconfigurations, weak protocols, and access control flaws across routers, switches, servers, and endpoints. We ensure compliance to many industry standards.
Wireless Network
We secure your Wi-Fi and wireless communication systems through targeted testing that identifies encryption flaws, authentication weaknesses, and connection protocol vulnerabilities.
API
We secure your APIs against data breaches and unauthorized access by identifying authentication flaws, injection vulnerabilities, and more in your API endpoints, ensuring compliance to standards like OWASP Top 10 and more.
Thick Client
We secure your desktop applications through thorough testing that identifies local storage vulnerabilities, communication protocol weaknesses, and authentication flaws that could compromise user data.

